Why Automated Detection Falls Short
Identifying corrupted files across large SharePoint environments requires methodical manual verification. Automated corruption detection faces significant limitations—preview functionality only works once files are downloaded locally, and even files showing previews may refuse to open when accessed.
Effective assessment requires a systematic approach: directory-by-directory review, manual file verification through individual downloads, timestamp analysis to correlate corruption patterns, and comprehensive documentation of affected directories and file types.
In this case, the corruption primarily affected finance and supplier contract directories—critical business documents that required immediate restoration to maintain operational continuity.
The Business Case for Granular Backup Architecture
Robust backup systems provide more than just data protection—they enable business continuity through precise recovery capabilities. The Johannesburg Synology backup system that resolved this crisis offered incremental backup architecture with detailed file modification timestamps, enabling exact point-in-time restoration.
Key technical capabilities included infinite time sliding through intuitive timeline interfaces, incremental change tracking that captured every file modification with precise timestamps, granular recovery options for individual file restoration without affecting unchanged documents, and seamless integration with SharePoint and OneDrive environments.
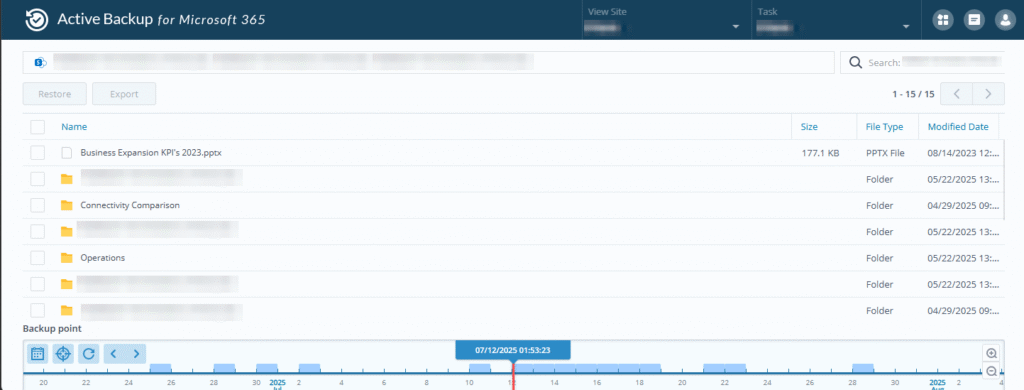
Strategic Recovery Methodology
Recovery required balancing comprehensive restoration with ongoing business operations. Since team members continued working on documents after the corruption incident, blanket restoration would have overwritten legitimate recent changes.
The strategic approach prioritised selective recovery: corruption timeline identification for files corrupted around specific dates, version validation to test historical versions for integrity before restoration, manual upload processes where automatic restoration encountered permission conflicts, and business continuity maintenance through immediate recovery of critical documents.
Measurable Business Impact Prevention
The systematic recovery process prevented significant business disruption across multiple operational areas. All supplier contracts and Master Service Agreements were successfully restored, preventing potential legal and operational complications from lost documentation. Critical finance records maintained integrity, ensuring continued compliance and operational reporting capabilities. Most importantly, team productivity remained largely unaffected due to rapid identification and systematic restoration processes.
Proactive Risk Management Strategy
Whilst this specific synchronisation scenario is challenging to prevent entirely—teams require multi-device access for productivity—several strategic approaches minimise similar risks.
Migration best practices ensure proper logout from synchronisation services before device transfers to prevent dual-synchronisation conflicts. Investment in backup systems with granular recovery capabilities provides essential protection against synchronisation-related data loss. Regular integrity monitoring through periodic manual verification of critical documents can identify issues before they become widespread.
The Integration Advantage
This incident demonstrates how systematic data protection approaches transform potential disasters into manageable recovery operations. Without proper backup architecture combined with methodical recovery processes, widespread synchronisation corruption could result in permanent loss of critical business documentation.
Si Futures’ integrated approach ensures backup systems, assessment methodology, and recovery processes work together seamlessly. We handle the IT complexity of data protection so you can focus on growing your business with confidence that your critical information remains secure and recoverable.
Contact our data protection specialists to discuss how systematic backup architecture can protect your business from synchronisation corruption incidents.

